I have a confession to make: I never took security too seriously. I’ve done the bare minimum of setting up 2-step authentication for my important accounts and using complex passwords, but the buck stopped there. I reused passwords. I used passwords for ungodly amounts of time without changing them. I didn’t respond fast enough to suspicious sign-in attempts, largely because they were on sites which I didn’t really have a strong need for. For all that was preached about security, I went a very long time without someone actually breaking in and doing any harm.
That is, until last week. I started receiving suspicious sign-in attempts on my Twitter account. My Microsoft account — which has thousands of dollars worth of digitally downloaded Xbox games tied to it — was also targeted. Someone tried hard to get into my Blizzard account where I’d spent hundreds of dollars on World of Warcraft and Hearthstone.
And then the kicker: someone actually knew the password to my Google account and attempted to sign in while I was asleep. Thank God I had 2-step authentication setup on it, otherwise they might have gotten access to, well, everything (more on that later). Oh, and as anyone following my Twitter account might have noticed, that was breached in the very same week.
I became a woman with a very kinky interest overnight.
Needless to say, all these incidents shook me up quite a bit. After all, 3 of the 4 services mentioned have my financial and personal information tied to them, and they all happened within days of each other — one might think someone was out to get me (or perhaps one of the passwords I use too often showed up in some of those leaked password lists).
But I digress. I couldn’t worry about who or why or when or how: all I knew was that my accounts were being hit one-by-one and that was enough to get me to change my ways. So here’s what I did about it.
First order of business: get a new mindset
The most important thing I did when all this went down was obtained a new mindset. Security is important, and it’s time I started acting like it. It shouldn’t have to take for you or myself or anyone to get hacked before realizing this, so I’m telling you now: get in gear before it’s too late.
When sites suggest you change your password often, take heed to that wise advice. When you sign up for a new site, don’t use the same password you’ve used for nearly everything else, and try not to use something that’s easily guessable. I know it’s tough to throw in those random numbers and odd characters for a password and you want something you don’t have to lookup, but it’s worth the inconvenience to make sure your accounts aren’t broken into on the back of sheer carelessness.
Thankfully there are great tools that can help strengthen and store your passwords so you don’t have to refer to those confusing combinations every time you want to log in. We’ll discuss the one I use shortly.
Next up was changing my Google password
I have a few email accounts for various reasons, but the one I use for nearly everything is sitting with Google. Email — work or otherwise — goes through there. I have chats on Hangouts with friends and family. My private photos are backed up to Google Photos. My Google account is where verification and forgotten password emails are delivered whenever my brain decides to forget everything.
Credit cards are stored on there for purposes of paying for apps, games, storage, and more. My banks, apartment manager, utility companies, internet and phone providers, and my healthcare providers all deliver their unsavory invoices straight to my financials folder.
There’s also the fact that someone actually knew the exact password to my Google account. All of that made it really obvious that this was the very first thing that needed to change. Even more than my bank accounts. For now, I decided to go with a 12-character password with a good variety of numbers, letters and casing, and I wrote it down temporarily as I looked to get a handle on other areas.
What about passwords for other accounts?
With Google out of the way, it was time to tackle other highly-sensitive accounts. I’ve got banks and healthcare logins. I have shopping accounts with over a dozen (maybe close to 2 dozen) retailers and merchants, including Amazon and Best Buy. I have credit card information with gaming vendors such as Sony, Microsoft, Blizzard, Epic Games, Hi-Rez Studios, Riot Games, Valve, and so on and so forth.
Holy crap, I have a ton of passwords to change, and I want them all to be unique and complex enough to pass those vague “strength” tests that show while you’re typing them in. Not only do I have to go through and change each password, I have to make sure they’re all stored somewhere secure. Well, paper and pen won’t cut it because I simply don’t have the time (or the space for the clutter). A text file — even stored inside an encrypted folder — isn’t much better.
That’s when the need for a powerhouse password manager app became apparent, and I set out on my search for one. There are a number of different things I was looking for in my password manager:
- It had to be fast and easy to use.
- At the same time, it had to be powerful enough for my changing needs.
- It had to be multi-platform.
- It had to be able to generate and store complex passwords.
- I had to have good faith in that platform’s underlying security.
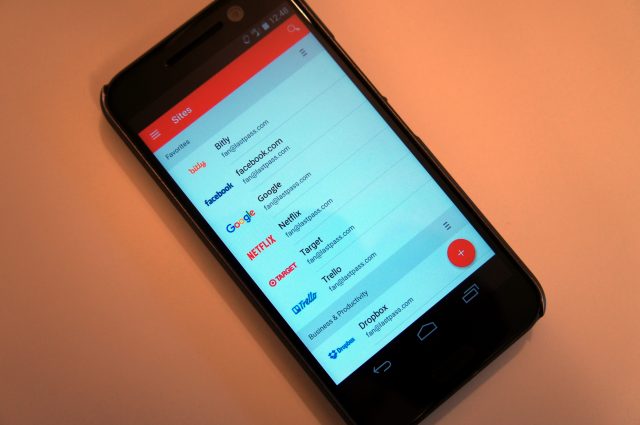
After much deliberation, I decided on LastPass. Simply put, it checks all of the above boxes well enough and I’m pretty happy with it. In my research, I did consider a recent incident with LastPass user data potentially being compromised, but oddly enough it was how they handled that incident that strengthened my decision: they were transparent. They shared exactly what was going on, what sort of information was compromised, and outlined ways they would make sure that sort of breach couldn’t happen again (and if it could, the damage would be minimal).
With my new weapon, I logged into every single site that I had an account for (over 80, not counting duplicates) and generated new strong 12-character passwords for them. Every. Single. One. LastPass has a feature that attempts to make this automatic, fast, and easy, but it doesn’t support every site, and even for the top sites it purports to support, the feature failed. (LastPass doesn’t promise that it’ll work for everyone.)
No worries — I had all day to sit there and get it done, and so I did. So, what’s next?
Setting up 2-Step Authentication
If you’ve been paying attention this far, you know that the 2-step authentication I have enabled on my Google account perhaps saved me from a world of hurt. If you’re not sure what 2SA is, I have a couple of steps that you need to take right now:
- Read up on 2SA and why it’s a very important element of any sort of authentication security right here.
- Sign into any account you have that supports 2SA and get it enabled as soon as possible.
But if you’re short on time, here’s a quick explanation courtesy of Google:
Most people only have one layer – their password – to protect their account. With 2-Step Verification, if a bad guy hacks through your password layer, he’ll still need your phone or Security Key to get into your account.
In my case, when I woke up the morning that I found my virtual doors wide open, I found a 6-digit code from Google sitting in my messages. Whoever had my password was able to sign in, but they weren’t actually granted access unless they had that specific code to input at the time that Google asked for it. Thus, they were simply locked out. Had I not set 2SA up, my Google account was all theirs for the taking, and I might be looking into identification theft services on top of all this.
Anyway, the point is that 2-step authentication is very much worth setting up. Some will argue that it’s still not the most secure method of multi-factor authentication out there, but it’s the most easily accessible and most easily enforced for everyday folks like you and I.
So, after getting all my passwords squared away, I sought out to ensure 2SA was enabled on all accounts that I could enable it on. I had most of the important sites squared away in that regard (which is probably why I was so careless about the importance of good password practice in the first place), leaving me with only a few stops to hit.
Pro Tip: Any time you can make an account, check to see if you can enable 2SA — it could be a life saver one day as it was for me.
Put sites on a need-to-know basis
In the military or any sensitive enterprise environment, one phrase pops up very often: you’re on a need to know basis. If you don’t need the information to do your job, then your company has no need to give it to you (as the risks of you leaking that information far outweigh its purpose for you and convenience for them).
So why not treat your online accounts that way? Does that gaming forum really need to know your address? Do you really need an impersonal birthday wish from Evernote every year? Has it been 3 years since you’ve shopped at CVS online? If the first 2 answers were no and that last one is yes, it’s probably a good idea to remove your information.
And that’s what I did. While I was changing those passwords, I reviewed my account information to see if there was anything on my profiles that I didn’t want or need there. I didn’t quite go to the extremes of removing birthdays or my full name (that’s all over Google by now anyway), but addresses and credit cards were definitely scrubbed clean from sites which I know don’t need them anymore. From now on, i’m also going to be adamant in making sure I’m not over generous in giving that stuff when signing up for new sites. Done, and on to the next thing.
Reciting my Vows
No, I’m not getting married, although all of this seems nearly as daunting as the preparation to do so. I’m vowing to commit to maintaining all of this, with two specific requirements:
- On sensitive accounts, change the password and check details a maximum of once every 30 days.
- On non-sensitive accounts, change the password and check details a maximum of once every 90 days
And to make sure I stay on top of it, I’ll have annoying Google Calendar reminders making my phone scream at me when the time comes. If it’s one thing I’ve learned, it’s that security is an ongoing concern for, well, everyone. Even if you use the most ridiculously complex password the first time, that doesn’t mean you don’t need to change it, or use unique passwords, or go to extra measures to ensure your information is safe even if the credentials somehow fall into the wrong hands.
It’s time to start my new life.
What do you do?
You might think I’m going a bit too far and being overdramatic. Or perhaps you’re already just as heady as me, if not more so. All in all, it took me a very significant chunk of a weekend (and then some) to accomplish all of this, but that’ll prove to be nothing compared to the time it would take me to get my life back in order if someone got their hands on my sensitive information.
But I’m curious — what’s your regiment? What steps do you take to make sure your accounts are secure and your passwords aren’t falling into the wrong hands? Is there something more (or more efficient) I could be doing? Let’s talk about it in the comments section straight ahead!















Comments