In the wake of talk of trojan Android applications and apps with permissions that could only mean malicious intent, a rather precarious situation has arisen. In what developer Brenton Klik is calling a permissions bug, apps that are designed to install on both the phone’s internal storage and onto the SD card may be authorizing additional permissions beyond what the user agrees to upon installation. The problem came to Klik’s attention when he received the following comment on his flashlight application:
“This download page only indicates that the app uses System Tools, but the Applications menu says it requires access to make phone calls. Uninstalled.”
Now, what the user is referring to is the applications request for permission to prevent the phone from sleeping. This is the only permission shown when installed from the Android Market, however when the user navigated over to the Application’s info page after installation two additional permissions were spotted, permissions that were not expressly granted.
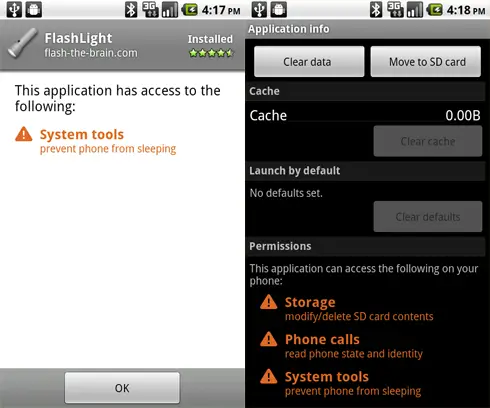
The first was permission to modify/delete contents of the SD card. Klik is correct in assuming this permission exists to allow users to move the app between phone storage and the SD card, but the fact that the wording of the permission is so broad leaves room for concern. The second unauthorized permission allows the app to “read phone state and identify,” which is slightly less disconcerting.
The fact remains that even if these permissions are granted without malicious intent and/or have no ability to really muck things up on your phone, they are permissions that the user is not asked to grant when installing the app, and in a world of security concerns and with the amount of personal data we carry on our phones the ease with which unknown permissions are granted doesn’t leave you feeling easy.
Then comes the ominous question posited by Mr. Klik: “If I’m gaining storage permission in this way, could I write an application that secretly or maliciously augments SD card data without the users [sic] knowledge?”
[via Flash the Brain]










This is such old news… Not a bug, fixed in sdk 4… Isn’t there any better news ?
No. The API for allowing app2SD allows SD access only in ways that allow the app to function. Adding in any other means of utilizing SD card information would require the app to request full SD read/modify permission.
If anything this is more of a permission reporting glitch on the app information page, as the app doesn’t have SD card access in the way they are reporting it.
Beat me to it ><
You need to read this reddit thread here about the issue: http://www.reddit.com/r/Android/comments/dapj1/this_crap_drives_me_crazy/
Basically, if you target Android 1.5, those permissions are automatically added without asking (because permissions didn’t exist until Android 1.6).
The solution is to set your target SDK to higher than Android 1.5 and set your min SDK to 1.5. This removes the permission problem. You just have to make sure to not call any APIs that are not available to 1.5 when you set your target to 1.6 or higher.
What if a app changes permissions with an update? Do you get a warning or it just installs cause you gave it permission when it was first installed.
To 5: No it won’t install it and you’ll have to manually update.
Though it doesn’t show the differences between permissions.
About reading phone identity, I assume this is so the user (every application on Android runs as a different user) will be able to decrypt the application when running it from the SD card.
The encryption key is part of the “phone identity”.
This whole thing is a wording/UI issue and not a security issue, at least from what I know.
Every time I update I get a list of permissions again.
As long as read-write permissions are unix-like, aka linux-style, you should be fine. App A shouldnt be able to read/edit sd contents on App B’s files. Unless you give it root permissions…
@adamsinger77 If an app changes permissions, it will not automatically update (if you’ve selected to do so) and will instead say “Update (manual)”.
Ahh got ya. I don’t think I ever paid attention after the manual updates any permission auth diag. Thanks for clearing this up.
I think the developers here have pretty much beat this dead horse. It is a symptom of backwards compatibility with compiling for 1.5 and adding the new feature of allowing an app to move to the SD card.
This isn’t a bug. The external storage and phone state permissions were added later so apps trying to be compatible with 1.5 are granted these permissions automatically.
@Gerg: the read-write permissions are not unix-like, because the filesystem on the SD card is FAT, which doesn’t have such permissions. This means that any app with SD permissions can read/write the files of other apps on the SD card.
I just tested this, and it works! It really does give you full access to the user’s SD card without asking their permission. Follow the articles via link to read what I did.
I made an app and video showcasing the exploit. You can view it here:
http://flash-the-brain.com/2010/09/market-exploit/
Brenton appears to be the only person with a clue here, everyone else is just speculating, missing the point, or just plain wrong.
If an app can gain full read/write/delete access to my storage, without my permission, simply by declaring that it wants Android 1.5, this is google-assisted malware and I would say it is good grounds to sue google.
scenario: Great, some random ‘game’ indexed and stole all my private documents and random nude photos of my wife off my SD card and broadcast them to the Internet. I never gave it permission to do that. What, google granted that permission automatically without notifying me? Well now, I think I will have very good grounds for a class-action lawsuit against google.
Oh, I just found out that in fact every app even without this exploit has full read access to the SD card. And so, I will not install any app that requests internet access, unless it is open source and I trust the author.