Ready for the next malware scare? Security firm Blue Coat Systems has uncovered a new form of malware that can attack an Android phone without the user having to do anything. Whereas usual malware attacks require the user install an APK or perform a specific action (which can sometimes be achieved with social engineering tricks), this particular exploit can be carried out with no user interaction — go to a website (the address is not yet disclosed, but we understand it’s a porn website) and you could be infected
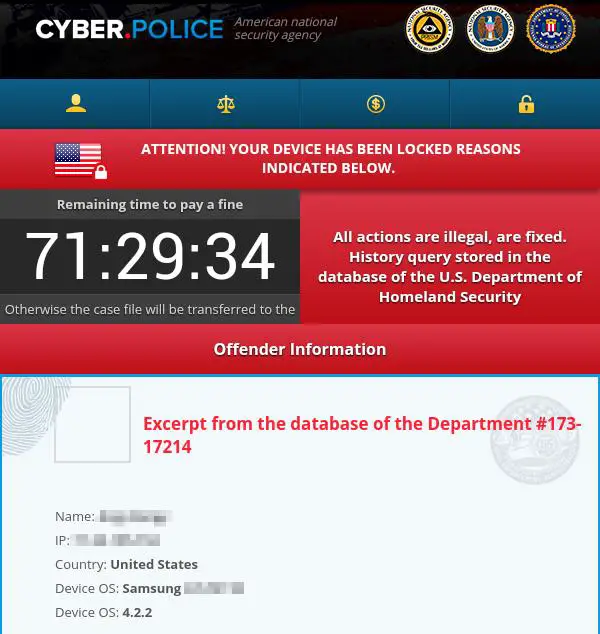
The initial ransomware screen when you are infected.
The attack takes sequential advantage of vulnerabilities found within Android. Many of those vulnerabilities were found and exploited in previous attacks on an individual basis, but not in such a way that would allow the code to spread to a device without user interaction.
Here are some of the specifics:
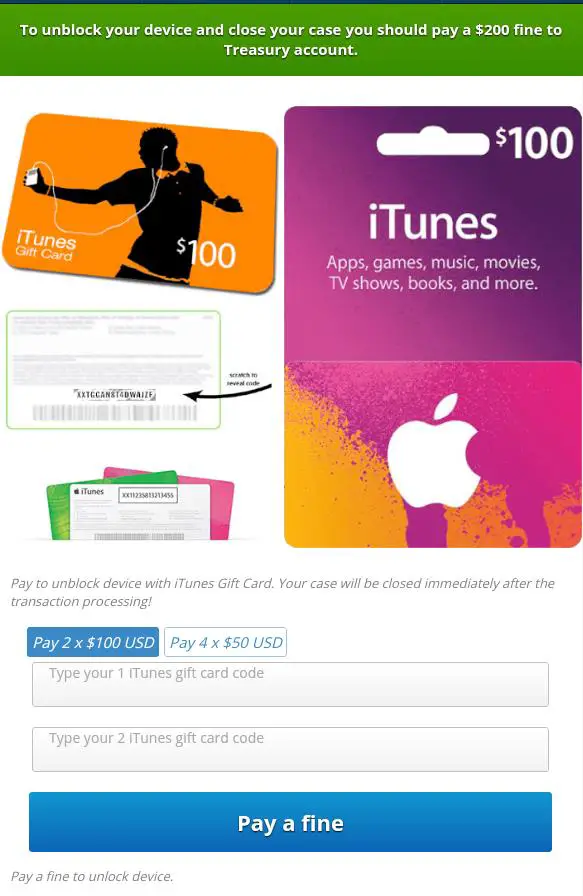
- The malware is more like ransomware, which is a type of virus designed to trick you into paying money to remove it. Remember those FBI child pornography viruses a while back? It’s something like that. They dress up like official government entities to scare the user into impulsively handing over cash. In this case, the Department of Homeland Security hilariously requests you pay them in iTunes gift cards.
- This particular malware only affects devices which have Android 4.0 through Android 4.3, but that still makes up for millions of Android phones out there. Another sequence of vulnerability attacks might also affect devices with Android 4.4.
- Users need only to visit a website with the code once and the malware may find itself on their phone without doing anything else.
- The malware can be removed with a factory reset and won’t persist.
The Ransomware asks for an iTunes gift card to gain access to your device.
The full report isn’t out yet, but it’s alarming nonetheless. Our guess is Google ended up plugging these holes long ago, but the fixes came only after the company retired Android 4.X to legacy status. It’s also possible Google issued fixes for Android 4.X devices, but the chances that an OEM would support an Ice Cream Sandwich or KitKat device at this point is very low, and so many devices remain vulnerable regardless.
If you still happen to be on a device with Android 4.0, be safe out there. Don’t visit a website unless you know you can trust it. These tips apply to all users, really, but those of you who can be targeted by something like this should be extremely cautious. And if you somehow find your device infected, take comfort in knowing that a simple factory reset is all you’ll need to recover it (even if it is annoying to do).
[via BlueCoat]









Comments