Micromax has been part of a lot of controversial conversations as of late, namely due to their role in the public fallout between CyanogenMod and OnePlus. But they’re less of an innocent bystander and more the accused instigator in these latest shenanigans: the company is reportedly remotely installing applications on users’ phones.
The revelation was first brought to light by Reddit user Redddc25, who’d found that his entry-level Micromax Canvas Fire (model number A093) has suddenly been loaded up with applications he didn’t install. Being that the device has very little internal storage — just 4GB — he quickly uninstalled them to save precious room.
And then they reappeared. Out of nowhere, apparently. Why? According to XDA, it’s due to a third-party OTA update service Micromax favors over the traditional route Google handles. The service’s app has code that makes it possible to automatically download and install applications without the user’s consent. Simply uninstalling them won’t help as, like we said above, they reappear after a short time.
To call this bloatware would be a bit of a long shot, while calling it spyware is borderline accurate. The difference between the two is that, in most cases in recent years, bloatware is typically pre-installed on the device and can either be disabled or completely uninstalled. We’ve always had a problem with bloatware, but it’s not shady — at least most companies are upfront about it.
But when you begin to abuse your power to influence a user’s device is when we begin to throw up the red flags. If a user is given the ability to uninstall an app, and they exercise their right to utilize that ability, they shouldn’t have to hear anymore of it. It should be gone, for good.
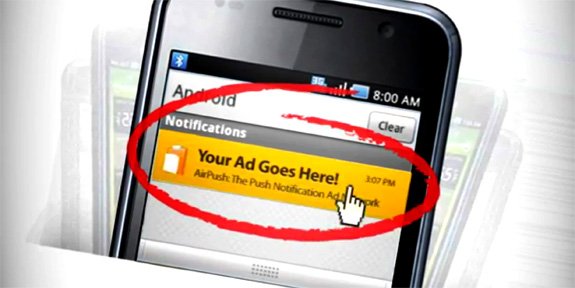
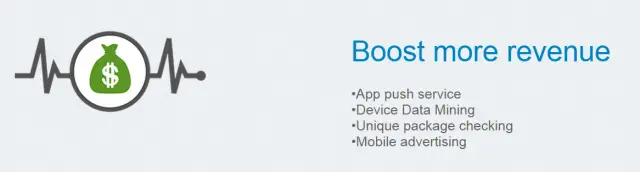
To make matters worse, the service doesn’t only install unwanted applications — it even litters your notification tray up with advertisements. You don’t begin to realize just how slimy it is until you hear the best part: the code reveals the website of the company who makes this OTA service, and they actually acknowledge the following “features”:
That list is about as scary as any bit of Android malware we’ve ever heard of (especially that whole “device data mining” part). There’s nothing that says for sure Micromax knows what’s going on with this service, but the general feeling so far by everyone who has an opinion to voice is that they do.
We’ll want to get their side of the story before taking that as gospel, but in the meantime XDA has provided a quick tutorial for Micromax owners to disable this functionality the only way they can (as it’s baked into a system app which can’t be disabled or uninstalled without root):
- Root your device. Google should help you find some appropriate root guides for your specific device.
- Download and install ADB. You’ll need this to issue a command. Here’s an easy ADB toolkit you can use to accomplish this.
- Issue the following command:
adb shell pm disable com.adups.fota
What this does is disable the OTA app from working, which should effectively stop those rogue app installations dead in their tracks. The downside is that this also hinders your ability to receive OTA updates, but it can easily be re-enabled with a similar command:
adb shell pm enable com.adups.fota
And that’s what you’re going to have to do until Micromax hopefully eradicates this issue and does away with this awfulness. Other OEMs, feel free to take note: this is not how you treat a device once it’s in the hands of your users.











Ironic that the Micromax logo contains a large image of a fist. Beautiful symbolism for the fisting that Micromax customers experience.
Where are the Anonymous guys when you need them? This is the perfect company to take offline with a DDos attack. Let them know what’s up.
Not your personal army.
No, but it wouldn’t exactly be unjustified to make them suffer some inconvenience for basically going all corporatocracy on people who bought their phones and expected to actually be able to control what is done with their own property. He never said he wanted them to do whatever he wanted. He just wants to see someone knock them down a peg for what they did.
Seriously? Who believe that MicroMax doesn’t know what the this company does? That’s exactly what they are looking for. Can anyone honestly say that MM didn’t do at least some minor research before signing on with them? This makes MM just a culpable as AdUps.
That’s what you get for buying a Micromax in the first place. Stay far FAR away from them!
SAMSUNG &/or T-MOBILE were/are guilty of the same shenanigans w/the NOTE4.
Along w/a minor update rode similar crapware/potential spyware that wasn’t on the phone brand new/out-of-the-box.
Ironic that KNOX is on-board as a “security” measure.
Rooted long ago & removed both.
That is a very different set of shenanigans.
Shifty, but not in the same class of shifty.
Thats what happens when you buy a crappy phone from a shady OEM.
If this turns out to be true and proved, I would blame Google for not cutting ties with a filthy OEM such this.
Google can’t just “Cut ties” with specific OEMS. Android is open source, meaning anyone who wants to use it can and Google can’t just say “No, we don’t like you.” And stop a company from using Android.
But they can prevent the company from using Google Play Services, which would cripple the device outside of China.
I hear you, but the framework belongs to google and google can deny them using it.
Airpush!? What is this? 2010?
Its Micromax, so yes
This is DT IGNITE on CRACK. °_°