Google in-app billing exploit allowed all-you-can-eat consumable content for free
An interesting exploit has recently been revealed by a developer who was tinkering around inside Google’s in-app billing libraries. Developer Dominik Schürmann discovered a method that would let people hijack the in-app billing method in such a way that would give them access to an app’s consumables without having to pay a dime.
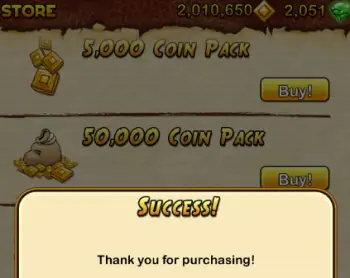
By consumables, I’m referring to items like coins in Temple Run or power-ups in Candy Crush — stuff that you can buy over and over again. As you can see in the image above, Dominik was successfully able to purchase an extreme amount of gems and coins in Temple Run 2, items that would normally cost hundreds of dollars to get in this amount.
According to Dominik, the exploit affects “all Google Play Billing Library v3 versions before Oct, 8 distributed via Android SDK and marketbilling on Googlecode.” That means Google was able to patch this thing up before word got out, but not without a tad bit of controversy.
According to him, Google chose not to credit him for the discovery, and sent emails to developers with information about the exploit (along with instructions to use recently updated sample code that addresses the exploit):
If you previously used the In-app billing sample code to build your in-app billing system, please use the recently-updated sample code as it addresses an exploitable flaw we recently discovered (note that this only affects the helper sample code; the core system and in-app billing service itself was not affected).
Disputes about proper attribution aside, I think everyone is still thankful that this has been patched up, and that no one will be able to leech free consumables from developers (as long as said developers make quick work of updating their code to the latest available sample). Those folks have to make money too, you know.
If you’re interested in the nitty gritty details (including ready-to-compile code and instructions on how to test this exploit) you can find them at Dominik’s blog. We just beg that you don’t use whatever you happen to find for evil.
[via Google+]