With the price of Bitcoin and other cryptocurrencies spiking high on tons of speculation, it’s no small surprise that Android malware has now shifted from farming clicks to farming bitcoins using your phone’s processing power. Security researchers at Kaspersky Lab have discovered a type of Android malware they’ve dubbed Loapi, based on its package name Trojan.AndroidOS.Loapi.
The trojan is usually hidden in apps that masquerade as anti-virus or cleaner apps for Android, while others were hidden in apps that resemble popular porn apps. These apps infected with the trojan actually feature several different modules that can be activated on the phone once it’s been granted permissions.
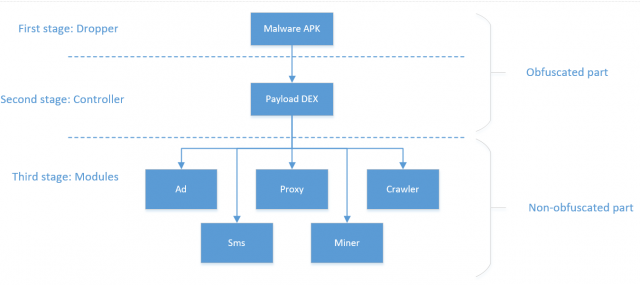
Researchers dubbed Loapi a jack of all trades trojan, since it’s possible for the malware to subscribe to paid services, send SMS messages to any number, generate traffic from advertisements shown to the user, and even uses your processor’s power to mine Monero, a type of cryptocurrency. Researchers mention the only module missing is a way to farm personal user data, but it could be added at any time.
To test the effects of this specific malware on a device, the researchers installed it on a test device and discovered the extra load from running a phone at 100% nearly all the time created a warped frame and battery bulge in the infected device.

These types of apps require the ability to download an app and run it from Unknown Sources, so that’s why it’s important to maintain security for your Android device. Family members who may not be that savvy with tech can easily fall prey to these malware prompts for permissions since they’re designed to loop repeatedly until permission is granted.












Comments