
What’s the back-up unlock method you use with your phone now that fingerprint readers are so common? Do you opt for the PIN method of unlocking your phone? That might not be as safe as you think it is, according to a new report that details how skilled attackers can determine a user’s PIN code by observing the fluctuations in a WiFi signal as the PIN is being used.
Here’s how the report describes the attack happening:
By setting up a rogue access point, determining the point in time when a user is entering a PIN (for the Alipay payment system in the demonstrated attack – the largest mobile payments company in the world), and observing the fluctuations in wifi signal, it’s possible to recover the PIN.
This new method of attack is a program called WindTalker and it’s unique because unlike other unique hacks that use audio recognition to determine which keys a person is pressing, or tracking hand movements over a smartwatch, it requires no access to the victim’s phone and it piggy-backs on existing wifi connections that are available.
WindTalker can monitor network traffic on any unsecured WiFi network, which attackers can then use to determine when a person is going to enter their PIN. That’s where WindTalker’s unique use comes into play.
WindTalker is motivated from the observation that keystrokes on mobile devices will lead to different hand coverage and finger motions, which will introduce a unique interference to the multi-path signals and can be reflected by the channel state information
Once that information is collected in the program, it can be cleaned up and compared to determine which numbers were a part of the PIN that was entered.
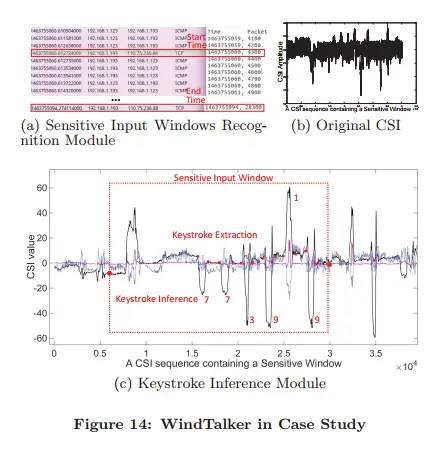
Now, before you go into panic mode and stop using PIN codes altogether, it should be noted that there are some caveats here. WindTalker needs some pre-training in order to capture codes with efficiency, but the article outlines sneaky ways that attackers can get you to do that pre-training, such as entering specific numbers to access a WiFi hotspot, or mimicking a text captcha to get you to input certain numbers.
Either way, this presents an interesting challenge that more mobile users should be aware of in public places like airports and cafes. Always be aware of what WiFi you’re connected to in unknown locations.







Comments