You decide you’re ready to try out that new fangled game that everyone is talking about. Mad Chickens, or something. You search, click, read some comments, click install. Before anything is installed to the phone you are greeted with a list of things this particular application has access to on your device and are asked to confirm that everything is OK and proceed to download and installation. Up until now that was all fine and dandy and you could rest easy in the knowledge that applications only had access to what you deemed appropriate.
All of that is out the window. A (massive?) security flaw has been discovered that allows a malicious application to access parts of a user’s device that it was never intended to have; and more frighteningly never declared they had the right to access. Malicious applications are nothing new to Android, but until now the user had to ignore what the application was requesting access to in order for the program to be installed.
“In the past, we’ve focused on the issue of users not paying attention to what permissions they’re approving for their apps,” says Oberheide. “But in cases like this, the attacker can bypass those permissions and it’s very difficult for users to protect themselves at all.”
The application in question is one that poses itself as a set of bonus levels for the not often talked about Angry Birds. When, in fact, it has nothing to do with the game. Once it is installed, the application is capable of installing other applications to the device that are malicious in nature. Note that I said “capable of”, not “it does”. Things like paid text messages and other bone tingling services that have the opportunity to hit the soft underbelly of you monthly bill if this exploit were to fall into the wrong hands.
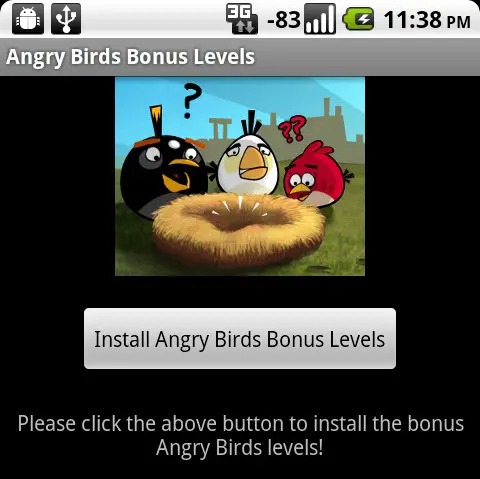
Thankfully, there is light at the end of this tunnel. Those that have discovered the vulnerability and created the spoof application are the good guys. The ones that want it patched, and are ready to demonstrate what the flaw is; hopefully not to the public. In a talk tomorrow at a security conference, hosted by Intel in Hillsboro, Oregon, the men who discovered the flaw will discuss their finds.
Just remember to read the comments and only install applications from trusted sources. A little common sense can go a long way; and if something doesn’t feel right, just back away.
[via Forbes]










I ALWAYS read both the comments and more importantly the permissions before downloading ANY new app to my phone. Apps that ask for too many permissions never get downloaded, no matter how useful the app may be. I’ve bypassed numerous apps for this reason alone. Great topic of discussion guys, thanks for posting it! I posted a comment earlier today regarding this very issue as it looked like too many people think our smartphones are immune to these types of attacks, and thats an extremely unsafe attitude to have. Thanks again Tyler!
Not to be rude, but I don’t really understand what you are trying to convey in your post. The wording is confusing and some words have been left out completely. It’s kind of annoying to read a post that has not been proofread. Anyway, I love your site and rely on it daily. Thanks for the hard work.
Like any other platform, you should always think about what you are downloading and installing. I understand that the market up until now has treated smart phones as appliances but they are more and more coming to resemble full fledged computers. Treat them accordingly and you should have no problems. I don’t get viruses on my computer because I don’t download and run random executables. My phone is no different.
I don’t download and run unknown executables either but I’ve picked up a few viruses over the years. There’s a lot of different ways to pick up a virus these days besides downloading apps/programs/etc.
Makes me kinda glad I hadn’t beat this game yet! But it was all the negative comments on the Market (and this site) that kept me from this update.
RE an earlier post this evening, it’s a good sign that AVG is entering the android field now. Whether or not it’s your favorite AV software on Fenestrum Septimus (Pardon my Latin. I only had one quarter in 8th grade. But I shall not name that fenestral OS in an android forum.), AVG brings a lot of experience and expertise to the android universe.
THANK YOU Drew! this is my constant critique of this site. the writers could proofread MORE! and maybe even go back and fix there typos… what a concept!
name it in English, that is.
People that complain about someones typos or grammer online have entirely too much free time on their hands and should seriously find a real hobby, because pointing out someones mistakes only makes you look anal. Take your OCD medication and move on.
Seriously, weiman…Seriously? If you aren’t going to proofread your own comments before submitting them at least site my errors. I’ve been over this post half a dozen times and can’t find what you people are complaining about. Too much time staring at your monitor, get some air.
@weiman
“maybe they should go back and fix THEIR typos…..”
Fixed it for ya. ;)
art: you’re feeding the troll. that was a troll.
@ Tyler Miller
I expected a more adult response from the editor of a major news website. Commenter ‘weiman’ was wrong to be rude, but that doesn’t mean you have to retaliate. We are just saying the post is a little confusing and often times this website does leave typos in the articles. What do I mean by confusing?
“Before anything is installed to the phone you are greeted with a list of things this particular application has access to on your device and are asked to confirm that everything is OK and proceed to download and installation.” – There is no punctuation and the sentence seems to run on leaving me lost at the end.
“Malicious applications are nothing new to Android, but until now the user had to ignore what the application was requesting access to in order for the program to be installed.” – It took me a couple of reads to undertand what you were saying here.
You also never tell us who this Oberheide fellow is. More confusion.
I love your site, but I just felt this article was generally confusing.
But it doesn’t help to point out someones typing errors when the people complaning are making just as many typos themselves. Makes one look like a real tool imo!
I’m an English major and I didn’t notice any glaring grammatical errors. Relax!
Security exploit aside, this also annoys me because I can hear the iphone fanboys now: “Your fragmented, ugly, ‘OPEN’ OS is now ‘OPEN’ for viruses har har har.”
Thank you for the heads up, hopefully they sort that out at the conference. Nice to know that intel is involved so at least some money might be behind it.
172 73H B1G L4N… 1F 172 700 K0Mpl1C473d PH0R U 70 unD3r574nd G7F0
Smells of trolls
I wouldn’t mind having the ability to edit my own posts, but I make no claim as a writer. Besides, I make no personal attack so need to be defensive. Take it with a grain of salt. My commentary is about the site as a whole. For example, the phone section was finally updated some months ago – it really did take forever. Aside from my gripes, I check the site frequently for Android news.
wiman : GFYS.
Correct me if I’m wrong.
“…until now the user had to ignore what the application was requesting access to in order for the program to be installed.” Users don’t have to ignore the permissions (though many do ignore them), but by proceeding to install the app the user is authorizing those permissions.
@Tyler Miller: “If you aren’t going to proofread your own comments before submitting them at least site my errors.” I’ll leave you to find the error I’ve cited.
@Tyler: I found your article (and generally the rest of the site) perfectly easy to read and grammatically sound, but ironically in your comment…
*cite :p
This has been quite obvious for a long time. Any one click root app, or any app that uses those exploits has the power to destroy your phone or steal your data.
You must lead a sad life Weiman. You’re bitching about the authors post and look at your last post #17. Read your second sentence and tell me you don’t make any typing errors. Incredible. Stop worrying so much about peoples typos and try focusing on the topic itself. Out of all your comments here you’ve had nothing to contribute to the story itself. That or change your name to whine-man.
I wonder if there is such an X_App that “blocks” certain permission when a particular Z_app is running. For instance, install a Z_app that wants permission to use Full Internet (or Full GPS Fine Co-ordinates, etc) and have the X_App to configure to ensure that Z_App does not access those permissions when executed?